Behavioral Threat Detection
Behavioral Threat Detection
Monitor usage patterns in real time to identify abnormal, risky, or compromised interactions before they escalate into security incidents.


Uncover threats hidden in user behavior
Behavior Threat Detection continuously analyzes how users interact with your LLMs to catch patterns that slip past prompt-based filters.
Multi-turn analysis
Track session evolution across multiple messages to catch complex exploit chains.
Anomaly scoring
Assign dynamic threat scores to sessions based on historical and real-time data.
Deviation detection
Identify behavioral outliers such as sudden prompt flooding, input structure changes, or tone shifts.
Intelligent blocking
Auto-block users, IPs, or sessions that exceed configurable threat thresholds.
Catch emerging risks across thousands of users
Detect coordinated attacks, abuse, or usage anomalies with high accuracy, even at peak volume.
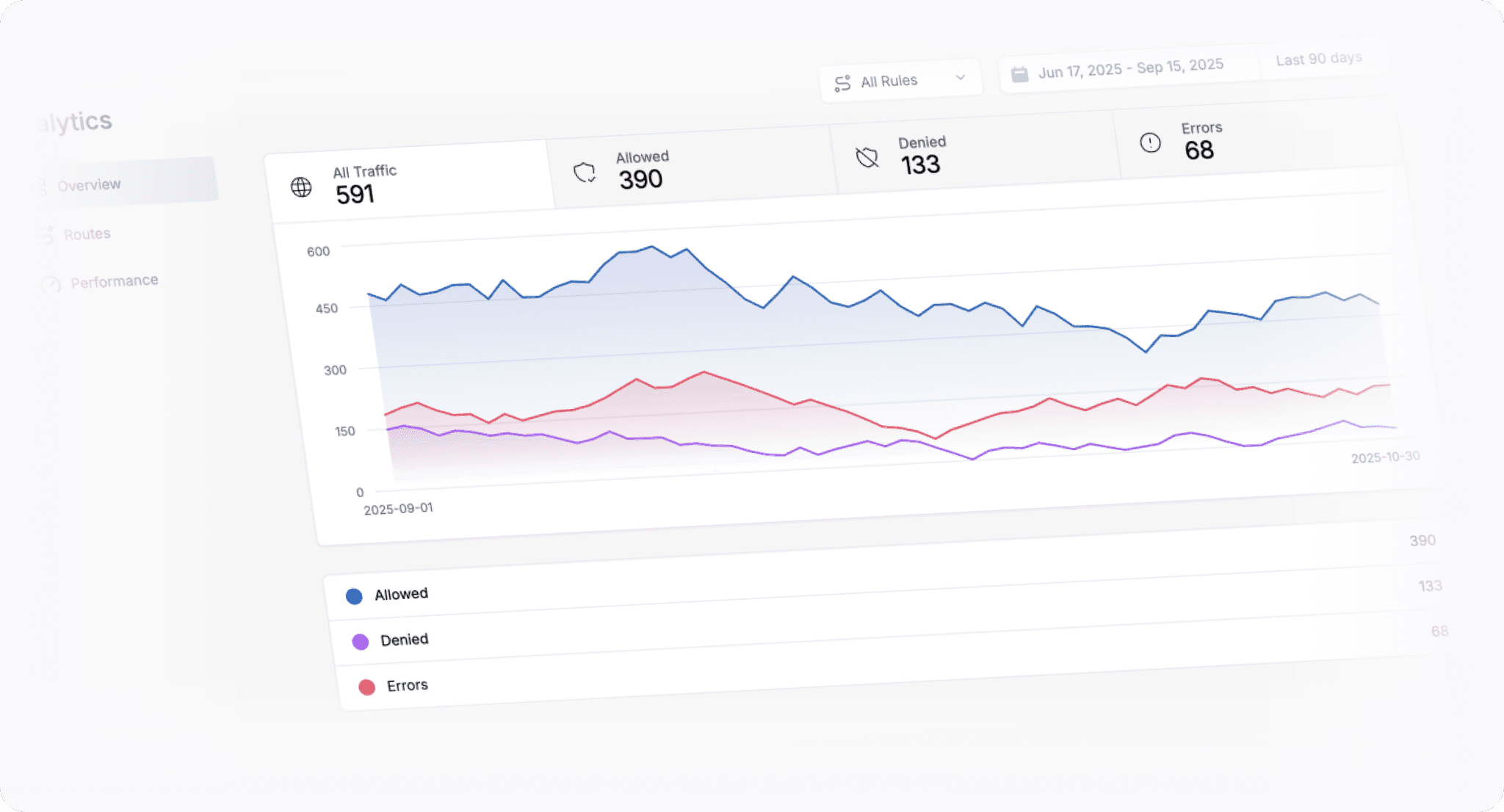

Monitor, audit, and respond with precision
Integrate Behavioral Threat Detection into your existing stack and workflows for real-time insights and response.

SIEM integration
Push alerts and session data into tools like Splunk or Prometheus for centralized security visibility.
Policy engine support
Pair with Moderation Policy Engine to enforce conditional rules based on threat behavior.
Granular observability
Trace every interaction, policy trigger, and block decision for forensic analysis and compliance.
Plugin-ready
Extend detection logic via custom plugins that adapt to your unique application landscape.
SIEM integration
Push alerts and session data into tools like Splunk or Prometheus for centralized security visibility.
Policy engine support
Pair with Moderation Policy Engine to enforce conditional rules based on threat behavior.
Granular observability
Trace every interaction, policy trigger, and block decision for forensic analysis and compliance.
Plugin-ready
Extend detection logic via custom plugins that adapt to your unique application landscape.


Secure your AI infrastructure today
Mitigate risks before they escalate through Runtime Security
Get a demo